Imagine you wake up to a frantic call from your PR team. News has broken. Your company is the latest victim of a major data breach. Millions of customer records, including sensitive financial data and personal information, have been compromised. The source? A discarded server that you thought was properly disposed of.
This is the nightmare scenario that keeps IT leaders up at night. And unfortunately, it’s a scenario that plays out with alarming frequency. While we invest heavily in cybersecurity to protect our active networks, we often overlook a critical vulnerability: improperly disposed of IT assets.

The Anatomy of a Data Breach: From Discarded Device to Disaster
Think that old hard drive sitting in a storage closet is harmless? Think again. Even after you’ve deleted files or formatted the drive, sensitive data can often be recovered using specialized software. That discarded server, laptop, or even a seemingly innocuous USB drive could contain a treasure trove of information for cybercriminals:
- Customer Data: Names, addresses, social security numbers, credit card details – everything needed for identity theft and financial fraud.
- Financial Records: Proprietary financial data, bank account information, and other sensitive documents that could cripple your business.
- Intellectual Property: Trade secrets, product designs, and confidential business plans that could give your competitors an edge.
- Employee Data: Personal information of your employees, potentially exposing them to risk.
When these assets are not properly disposed of, they can fall into the wrong hands at various points in the disposal chain. Scavengers, unethical recyclers, or even hackers specifically targeting discarded equipment can recover the data and use it for malicious purposes.
The Cost of Non-Compliance: More Than Just a Fine
The consequences of a data breach stemming from improper ITAD are severe and far-reaching:
- Financial Penalties: Violating data protection regulations like GDPR and HIPAA can result in massive fines, potentially reaching millions of dollars.
- Legal Fees: Expect a hefty bill from lawyers as you navigate the legal ramifications of a breach, including potential lawsuits from affected customers.
- Operational Disruptions: Dealing with a breach takes time, resources, and manpower, diverting your IT team from critical business operations.
- Recovery Costs: You’ll face expenses related to data recovery, forensic analysis, credit monitoring for affected individuals, and implementing new security measures.
Reputational Fallout: The Unseen Damage
Perhaps the most devastating consequence of a data breach is the damage to your company’s reputation. News of a breach can spread like wildfire, eroding customer trust and damaging your brand image. The loss of confidence can lead to:
- Lost Customers: Customers may take their business elsewhere if they don’t trust you to protect their data.
- Damaged Brand Equity: Years of building a positive brand image can be undone in an instant.
- Negative Media Coverage: A data breach can generate negative publicity that’s difficult to recover from.
- Loss of Investor Confidence: Shareholders and investors may lose faith in the company’s ability to manage risk.
American Steed: Your Shield Against the Data Breach Nightmare
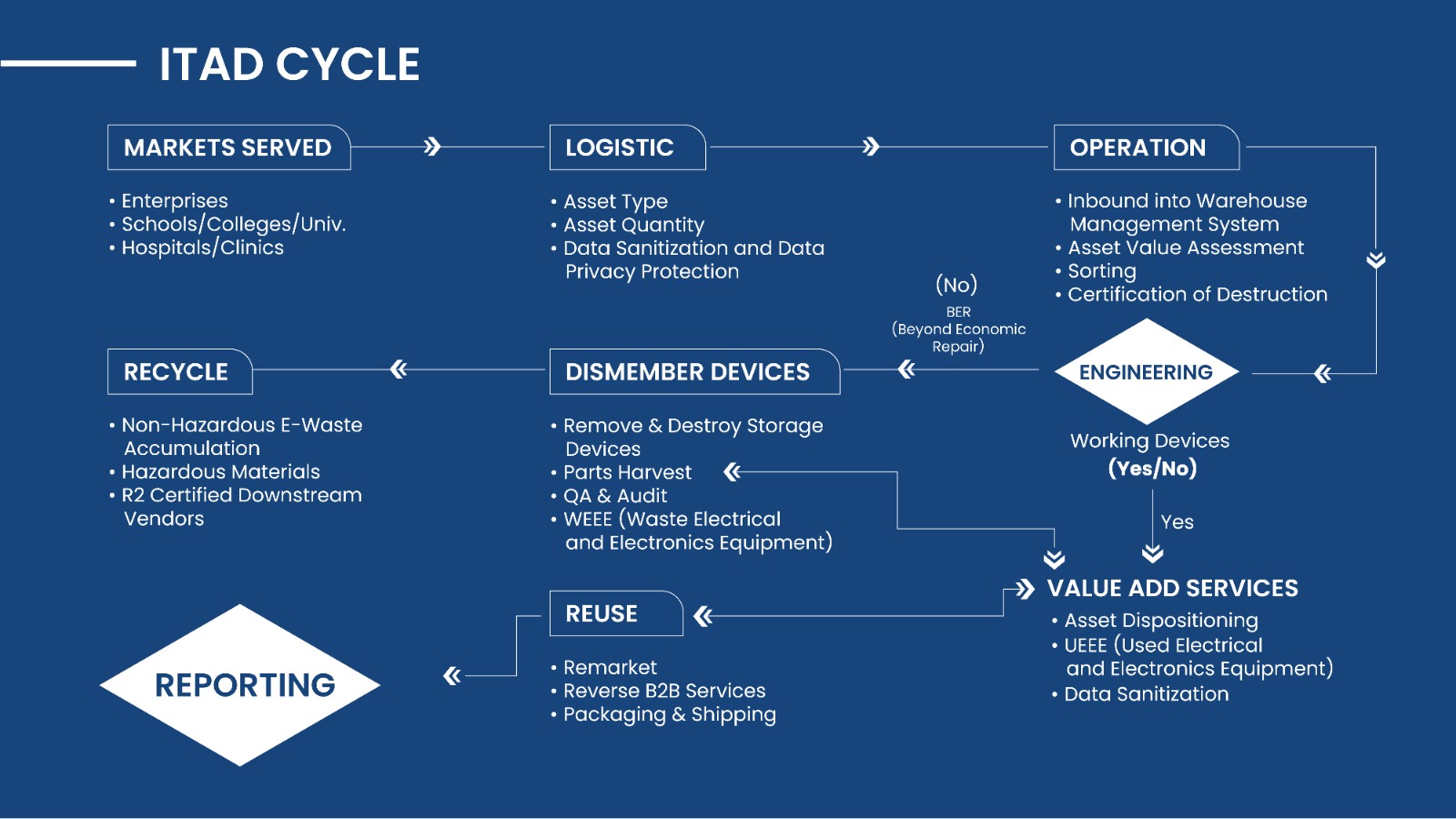
At American Steed, we understand the critical importance of secure IT asset disposition. We provide comprehensive ITAD services that eliminate the risk of data breaches from discarded equipment, giving you peace of mind and protecting your business from financial and reputational harm.
Our certified data sanitization processes ensure that all data on your retired assets is completely and irreversibly erased, exceeding the standards set by GDPR, HIPAA, and NIST 800-88. We utilize industry-leading techniques, including:
- Multi-pass Overwriting: We overwrite data multiple times with random patterns, making it virtually impossible to recover.
- Degaussing: We use powerful magnetic fields to completely erase data from magnetic storage media.
- Physical Destruction: For highly sensitive data or damaged media, we offer physical destruction methods like shredding or crushing.
Beyond Data Security: A Comprehensive Approach
American Steed’s ITAD services go beyond just data destruction. We offer a holistic approach that includes:
- Secure Logistics: We provide secure transportation and a documented chain of custody for your assets.
- Value Recovery: Through our asset remarketing program, we help you recoup value from your retired IT equipment, turning a potential liability into a revenue stream.
- Environmentally Responsible Recycling: We partner with certified e-waste recyclers to ensure that your assets are disposed of in an environmentally sound manner.
Don’t Let Your Discarded IT Assets Become Your Biggest Liability
The risks of improper IT asset disposal are simply too great to ignore. Protect your data, your reputation, and your bottom line by partnering with a trusted ITAD provider.
Contact American Steed today for a free consultation and learn how our secure and compliant ITAD solutions can help you avoid the data breach nightmare.
Click Here to Schedule a Free Consultation









Comment (1)
The prose evokes gentle observation. Ordinary moments are rendered extraordinary through careful attention, encouraging mindfulness and appreciation for subtle detail.